Understanding Fabric CA Structure and Its Comparison with Traditional CAs
Introduction
Hyperledger Fabric's Certificate Authority (Fabric CA) is a specialized implementation of a certificate authority designed specifically for blockchain networks. While it shares many fundamental principles with traditional Certificate Authorities, it includes unique features tailored for distributed ledger environments. Understanding these similarities and differences is crucial for blockchain architects and developers working with Hyperledger Fabric.
Key Takeaways
- Fabric CA follows traditional PKI principles while adding blockchain-specific features
- Both traditional and Fabric CAs use hierarchical structures for certificate management
- Fabric CA includes additional components for identity management in blockchain networks
- The registration and enrollment process in Fabric CA is specifically designed for distributed networks
- Both systems rely on similar cryptographic principles but serve different use cases
Understanding the Structures
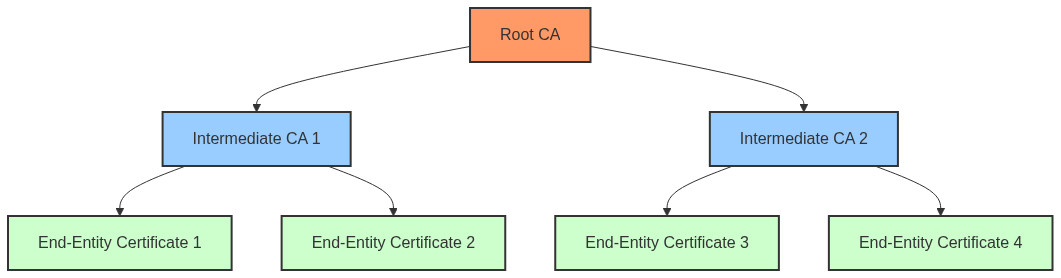
Traditional CA Structure
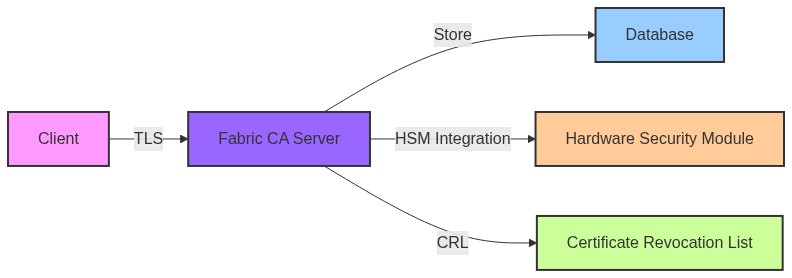
Fabric CA Structure
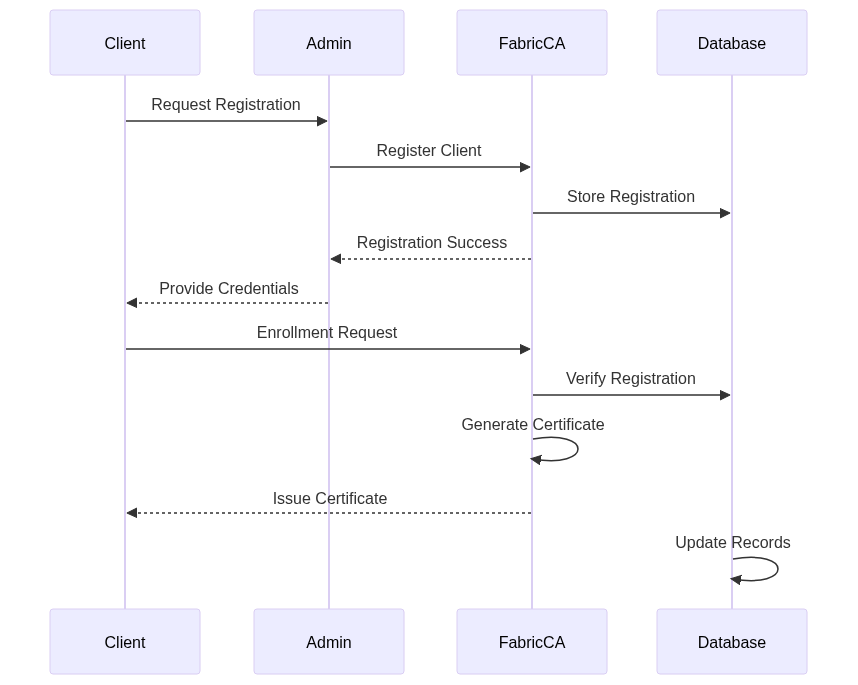
Certificate Lifecycle Process
Core Components Comparison
Traditional CA Components
-
Root CA
- Highest level of trust
- Self-signed certificate
- Typically offline for security
-
Intermediate CAs
- Issued by Root CA
- Handle day-to-day certificate issuance
- Can be chained
-
Registration Authority
- Verifies identity
- Processes certificate requests
- Forwards to CA for signing
Fabric CA Components
-
Fabric CA Server
- Issues certificates
- Manages identities
- Handles revocation
-
Fabric CA Client
- Interacts with CA server
- Manages enrollment
- Handles certificate renewal
-
Database Backend
- Stores identities
- Maintains certificates
- Tracks revocation status
Security Architecture
Key Similarities
-
Hierarchical Structure
- Both use Root and Intermediate CAs
- Trust chains are similar
- Certificate validation follows same principles
-
Cryptographic Foundation
- X.509 certificate standard
- Public key infrastructure
- Digital signature algorithms
-
Security Practices
- Private key protection
- Revocation mechanisms
- Audit logging
Key Differences
-
Identity Management
- Fabric CA includes blockchain-specific attributes
- Support for MSP configuration
- Organization-specific features
-
Authentication Methods
- Fabric CA uses enrollment ID and secret
- Custom attributes for blockchain roles
- Network-specific access controls
-
Integration Capabilities
- Direct blockchain network integration
- Smart contract support
- Channel-based privacy
Real-World Implementation Examples
Traditional CA Use Case
Fabric CA Use Case
Frequently Asked Questions
Q: Can a traditional CA be used instead of Fabric CA? A: While technically possible, traditional CAs lack blockchain-specific features and integration capabilities that Fabric CA provides.
Q: How does certificate revocation differ between traditional and Fabric CA? A: Fabric CA includes blockchain-specific revocation mechanisms and immediate network-wide propagation through channels.
Q: What additional security features does Fabric CA provide? A: Fabric CA includes features like attribute-based access control, MSP integration, and blockchain-specific identity management.
Q: How does scaling work in Fabric CA compared to traditional CAs? A: Fabric CA is designed to scale horizontally across organizations in a blockchain network, while traditional CAs typically scale vertically.
Q: Can Fabric CA certificates be used outside the blockchain network? A: Yes, Fabric CA certificates follow the X.509 standard and can be used for general-purpose PKI, though they contain additional attributes specific to Fabric.
Conclusion
While Fabric CA builds upon the proven principles of traditional certificate authorities, it extends these concepts with blockchain-specific features and capabilities. Understanding these similarities and differences is crucial for implementing secure and effective identity management in Hyperledger Fabric networks. The specialized features of Fabric CA make it particularly well-suited for enterprise blockchain deployments while maintaining compatibility with established PKI standards.